User Manual
User Manual
Privacy
How does Ironchip deal with privacy?
Ironchip develops all products by following the privacy by design framework, meaning we build privacy into our solutions at all levels, from idea conception to product launch.
Our technology was developed in a way that prevents access to information capable of re-identifying users. Ironchip does not collect unique static device identifiers (such as IMEI and MAC), associated accounts (e-mail and telephone), civil identification data (name and social security number), or sensitive data – information that reveals ethnicity, religion, political opinion, religious, philosophical, political or union entities membership, and data regarding health, sex life, genetics, and biometrics.
Our solution requires the collection of data from mobile devices through an SDK. Once authorized, the Ironchip SDK starts to collect data without personally identifying any users.
Users can deny data collection by opting-out, which disables data collection for them.
For more information, please read our privacy policy.
Concepts
Bussines
Transaction
Any client initiated action that needs to be analized for fraud detection.
Report
The written analysis of the transaction that specifies the fraud case.
Report Details
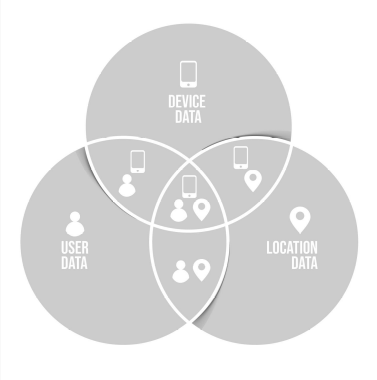
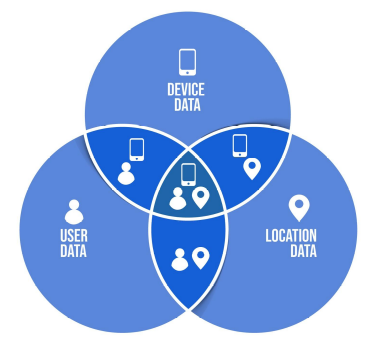
The context used for the report generation including:
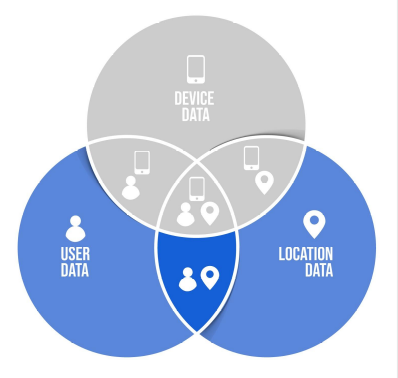
- The user, device and location information.
- Related transactions (transactions with common user, device or location)
- Users that have used the same device before.
- Users that have been reported in the same location before.
Report Case
The different results an analysis can report based on the use cases.
Device integrity
Fake GPS and Root (or jailbreak) information is sent through the Ironchip SDK to determine device integrity.
Fake GPS refers to mobile applications that are used to define a fake location on a user’s device. As a result, applications installed on the device will receive illegitimate location data in place of the actual location data.
Root (or jailbreak) refers to the rooting process that enables full access to everything on your mobile operating system. Full access means, more specifically, access to permissions that allow changing advanced elements in the device system.
Important
Tips: The greatest risk of Fake GPS for companies is its use for fraud, where people can, for instance, pretend to reside where they do not reside, perpetrate identity fraud, and mislead market intelligence by enabling false inferences.
A rooted phone is unable to receive official updates, but at the same time, it allows the user to manipulate the device at will. Modified devices may contain malicious applications and modifications for fraud purposes.
We apply different methodologies to identify forged GPS data or rooting and jailbreaking signals. The methodologies used are part of the data sent by the Ironchip APIs in several of our Use Cases.
Identifiers
Application ID
An Application ID is the identification number used by the Ironchip SDK to identify your app.
Warning
Note: This ID is generated by Ironchip and cannot be changed.
Transaction ID
The Transaction ID uniquely identifies each transaction – it is an ID generated by Ironchip’s customers to represent each unique transaction of their app. It is a required field for the Transaction API and it is used with the Report API to track the transaction.
User ID
The User ID uniquely identifies each user account – it is an ID generated by Ironchip’s customers to represent each unique user of their app. It is a required field for the Transaction API and it is used with the Report API to track who mades the transactions.
Behaviours
New User
Warnings
Device Swapping
This type of behavior occurs when the user does not use his usual device.
Result
Warning, device swapping.
Example
User makes a transaction with a new device.
Requirements:
- User-1 is required to be registered
- Device-2 is required to be new device
Procedure
- User-1 does a login and transfer with Device-1
- User-1 makes a login and a transfer with Device-2 from Location-1
Location Swapping
This type of behavior occurs when the user does not use his usual location.
Result
Warning, location swapping.
Example
User makes transaction from another user’s usual location.
Requirements:
- User-1 is required to be registered and and it has made transfers.
- User-2 is required to register with a new device.
Procedure:
- User-1 makes login and transfer from Location-1
- User-2 register with new device
- User-2 makes login and transfer from the same location as User-1
Frauds
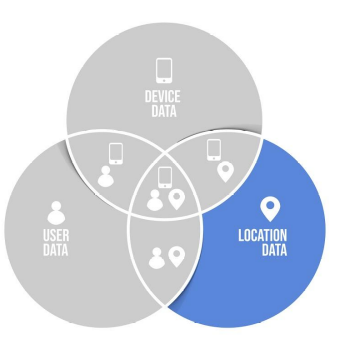
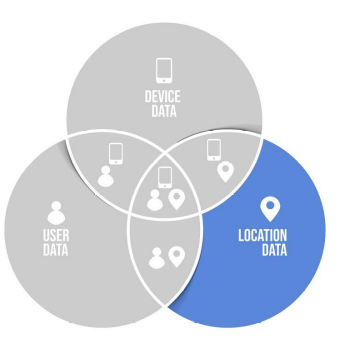
Location Fraud
Ironchip is capable of detecting location fraud. This is possible because when a location is registered, its radioelectric fingerprint is stored and will always be related to a geoposition. In the following operations these two variables will always be compared and if they do not match it will be assumed that the location is fraudulent.
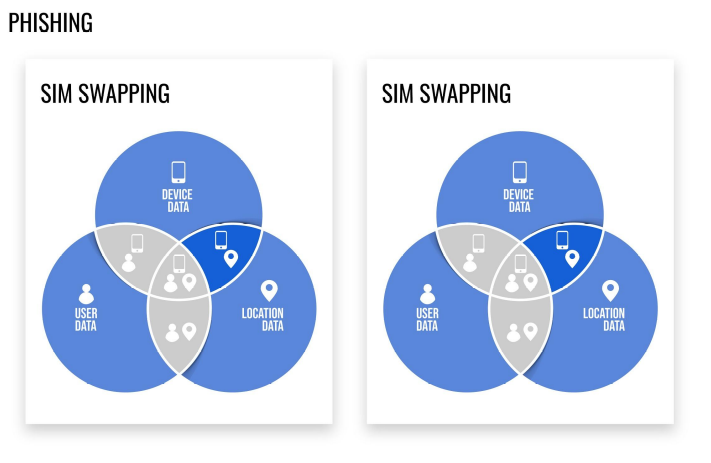
Phising
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker repeatedly defrauds by means of SIM Swapping.
Result
Fraud, Phising.
Example
A user makes a transaction with another user’s device and from unusual location.
Requeriments
- User-1 is required to be registered
- User-2 is required to be registered
- Location-3 is required to be a new location
Procedure
- User-1 makes a login and a transfer with Device-1
- User-2 makes a login and a transfer with Device-2
- User-2 makes a login and a transfer with Device-1 from Location-3
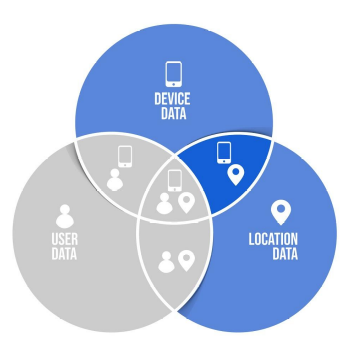
Sim Swapping
SIM swapping fraud is an account takeover scamthat targets a weakness in some forms of two-factor authentication in which a call or text message sent to a mobile telephone is the second factor or step.
Result
Fraud, SIM Swapping.
Example
A user makes transaction with another user’s device and from usual location.
Requeriments
- User-1 is required to be registered
- User-2 is required to be registered
Procedure
- User-1 makes a login and a transfer with Device-1 from Location-1
- User-2 makes a login and a transfer with Device-2 from Location-2
- User-2 makes a login and a transfer with Device-1 from Location-1
Synthetic Identity
Synthetic identity fraud (SIF) is the use of a combination of personally identifiable information (PII) to fabricate a person or entity in order to commit a dishonest act for personal or financial gain; i. e. a combination of fabricated credentials where the implied identity is not associated with a real person.
Result
Fraud, synthetic identity.
Example
A new user registers using a device already registered by another user.
Requeriments
- User-1 is required to be registered and it has made transfers
- User-2 is required to register with User-1’s device
Procedure
- User-1 makes a login and a transfer with Device-1
- User-2 register with Device-1
- User-2 makes a login and a transfer with Device-1.